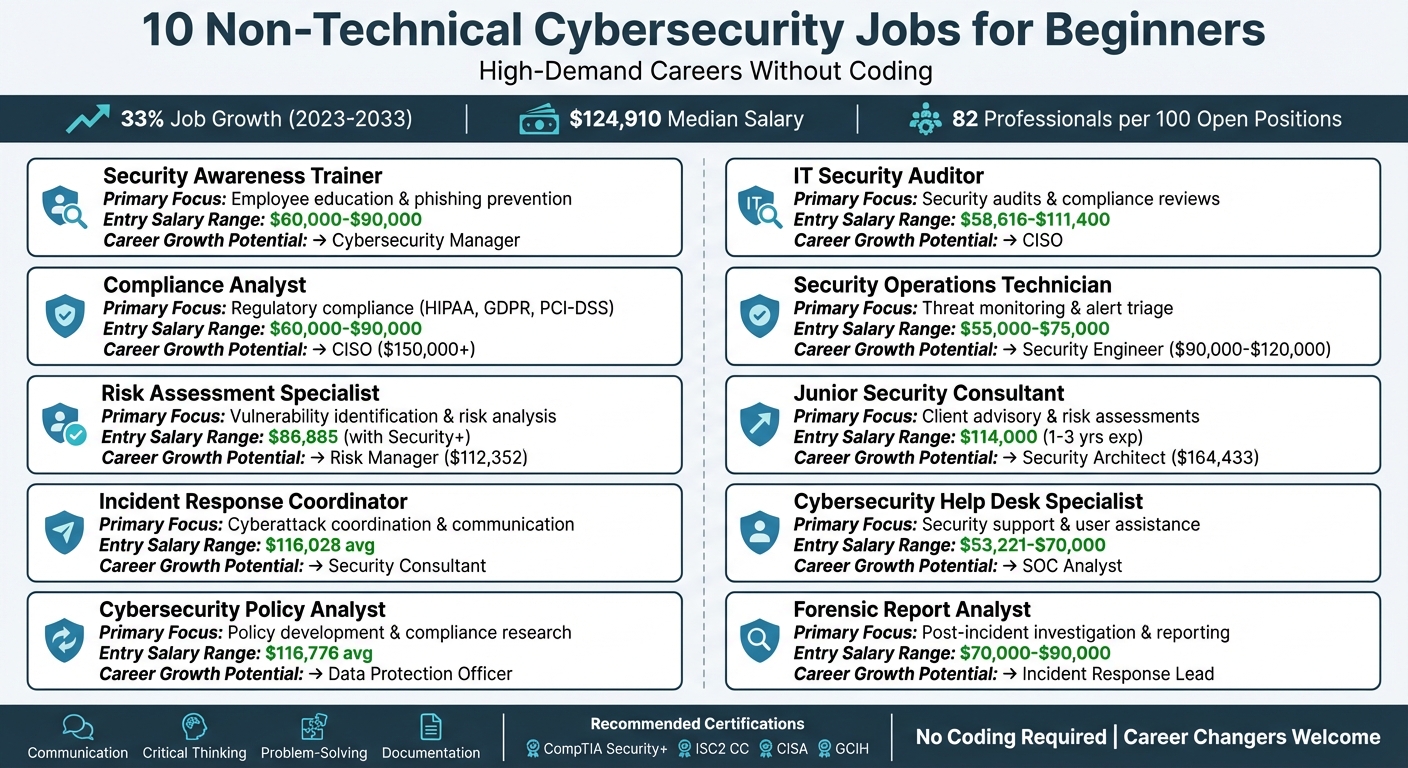
Cybersecurity isn’t just for coders or tech experts. In fact, most security breaches happen because of human error, not technical flaws. This means the industry needs professionals skilled in communication, policy analysis, training, and risk management. With job growth projected at 33% from 2023 to 2033 and a median salary of $124,910, now is a great time to explore non-technical roles in this field. Here’s a quick look at 10 beginner-friendly cybersecurity jobs that don’t require coding:
- Security Awareness Trainer: Educates employees on avoiding phishing and scams.
- Compliance Analyst: Ensures companies follow regulations like HIPAA or GDPR.
- Risk Assessment Specialist: Identifies potential vulnerabilities and recommends solutions.
- Incident Response Coordinator: Manages and organizes responses to cyberattacks.
- Cybersecurity Policy Analyst: Develops and updates security policies to align with laws.
- IT Security Auditor: Reviews security practices and ensures compliance.
- Security Operations Technician: Monitors systems for threats and escalates issues.
- Junior Security Consultant: Advises organizations on improving security practices.
- Cybersecurity Help Desk Specialist: Resolves security-related issues for users.
- Forensic Report Analyst: Investigates cyber incidents and prepares reports.
These roles focus on skills like communication, problem-solving, and critical thinking, making them accessible to career changers or those without technical degrees. Certifications like CompTIA Security+ can help you stand out. With a global shortage of cybersecurity professionals, this is your chance to step into a high-demand, well-paying career.
10 Non-Technical Cybersecurity Jobs: Roles, Salaries, and Career Paths
1. Security Awareness Trainer
Job Description
A Security Awareness Trainer plays a crucial role in helping employees understand and navigate cybersecurity threats. By breaking down complex technical ideas into simple, relatable terms, they focus on the human side of security. Their job is to teach staff how to spot phishing emails, steer clear of social engineering scams, and stick to the company’s security policies. The ultimate goal? To strengthen the organization’s first line of defense - its people.
Key Responsibilities
- Develop and deliver tailored security training programs for various teams.
- Create phishing simulations to test and improve how employees respond to threats.
- Produce engaging educational materials like newsletters, videos, and presentations.
- Monitor training participation and effectiveness, ensuring compliance with industry standards.
Relevance for Beginners
This role is a great fit for those with backgrounds in teaching, marketing, public relations, or corporate training. The focus here is less on technical expertise and more on skills like public speaking, clear communication, and understanding others’ perspectives. If you’re good at explaining things and connecting with people, this could be your entry point into cybersecurity.
Potential Career Growth
Starting as a Security Awareness Trainer opens doors to broader opportunities in cybersecurity. You’ll build a strong understanding of security principles, which can lead to roles in areas like cybersecurity management, policy development, or risk and compliance. It’s a stepping stone for exploring diverse, non-technical career paths in this growing field.
2. Compliance Analyst
Job Description
A Compliance Analyst plays a critical role in ensuring that a company’s systems and digital assets adhere to federal and state laws, industry standards, and internal policies. They act as the bridge between technical IT teams and senior management, aligning efforts to protect sensitive information. While they don’t typically perform hands-on technical tasks, their focus lies in managing documentation, conducting audits, and ensuring regulatory compliance. Rob Carson, CEO of SemperSec, explains:
A security compliance analyst is an integral part of the security department of a company. He or she reviews policies to maintain informational integrity.
This responsibility forms the core of what a Compliance Analyst does.
Key Responsibilities
Compliance Analysts are tasked with organizing and leading security audits for regulations like HIPAA, PCI DSS, and SOX. They document security controls, evaluate data security risks, and suggest ways to address vulnerabilities. Their work often includes designing corrective measures for identified deficiencies and coordinating with third-party consultants to conduct independent audits. For publicly traded companies, they also ensure compliance with SEC requirements by disclosing material cybersecurity incidents.
Relevance for Beginners
If you’re someone who prefers managing processes over writing code, this role could be a great fit. A background in business, law, accounting, or even English can be beneficial, as the job requires simplifying complex regulations into clear, understandable documentation for non-technical teams. Entry-level positions in this field typically offer salaries ranging from $60,000 to $90,000 per year. It’s an excellent starting point for those looking to grow into roles in risk management or executive-level compliance positions.
Potential Career Growth
A career as a Compliance Analyst can open doors to higher-level roles like Risk and Compliance Manager, which offers salaries between $90,000 and $120,000. With experience, professionals can advance to executive positions, such as Chief Information Security Officer (CISO), where salaries often exceed $150,000. The demand for compliance professionals is strong, with employment for information security analysts expected to grow by 32% from 2022 to 2032.
3. Risk Assessment Specialist
Job Description
A Risk Assessment Specialist, also known as a Junior Information Risk Analyst, focuses on identifying potential threats and vulnerabilities within systems. Unlike roles that require coding, this position leans heavily on analytical thinking. As Mike Meyers, an author at Infosec Skills, explains:
"It's important to understand how the systems work before you can secure them."
This makes the position an excellent entry point for individuals transitioning from fields like business, law, or management.
Key Responsibilities
The primary duties of a Risk Assessment Specialist include evaluating risks during system changes, identifying vulnerabilities, and documenting both initial and residual risks. They also monitor how well security controls perform and pinpoint weaknesses in security architecture. Their recommendations often focus on preventing attacks such as phishing, malware, and ransomware. While technical programming skills are not the focus, strong communication skills are essential, as much of the job involves presenting findings to stakeholders. These responsibilities lay the groundwork for a fulfilling career in cybersecurity.
Relevance for Beginners
This role is particularly suitable for beginners, especially those coming from nontechnical fields like business or political science. It provides hands-on experience with cybersecurity basics through risk analysis. Entry-level positions often require knowledge of frameworks like the Risk Management Framework (RMF) and NIST standards. Foundational certifications such as CompTIA Security+ (with an average salary of $86,885) or GIAC Security Essentials (GSEC) can help candidates meet these requirements. With only 82 cybersecurity professionals available for every 100 open positions in the U.S., the demand for these roles is incredibly high.
Potential Career Growth
Starting as a Risk Assessment Specialist can lead to advanced roles like Cybersecurity Risk and Compliance Manager (average salary: $112,352) or IT Auditor (average salary: $108,163). With job growth projected at 32% from 2022 to 2032 and the costs of cybercrime continuing to rise, professionals in this field are more essential than ever.
4. Incident Response Coordinator
Job Description
Incident Response Coordinators are on the frontlines during cyberattacks, focusing on swift action to manage and resolve incidents. Unlike roles that require deep technical coding knowledge, this position prioritizes coordination and communication. These professionals act as a bridge between technical teams, management, and external stakeholders, ensuring smooth and organized responses to incidents. Their role is critical in maintaining clarity and order during potentially chaotic situations.
Key Responsibilities
In this role, coordinators monitor network traffic and system logs to detect potential security threats, isolate compromised systems to contain risks, and act as intermediaries between IT teams, security operations, and leadership. They also prepare post-incident reports, translating complex technical details into language that non-technical audiences can easily understand. Additionally, they perform root cause analyses to recommend steps that can prevent future incidents. The average salary for incident responders in 2025 is projected to be around $116,028 annually, with top earners making up to $186,000.
Relevance for Beginners
This position is often viewed as an excellent entry point for individuals with strong organizational and communication skills, even if they lack extensive technical backgrounds. With 59% of organizations reporting a shortage of cybersecurity staff, demand for these roles is substantial. Beginners aiming for this role should consider certifications like CompTIA Security+ or GIAC Certified Incident Handler (GCIH). Building a portfolio that demonstrates the ability to clearly document and explain technical information can also give candidates a competitive edge.
Potential Career Growth
Starting as an Incident Response Coordinator can open doors to more advanced cybersecurity roles. It’s a stepping stone to positions like Penetration Tester, Security Consultant, Malware Analyst, or Cybersecurity Manager. With the cybersecurity industry expected to grow by 29% between 2024 and 2034, the opportunities for career progression are abundant. As Ed Moyle puts it:
"The incident responder role also provides a perfect starting point for future career growth. Moving from incident response to virtually any other security or security-adjacent position is a natural step."
5. Cybersecurity Policy Analyst
Job Description
Cybersecurity Policy Analysts focus on evaluating and updating security policies to ensure they align with current laws, industry standards, and organizational objectives. Unlike technical roles, this position emphasizes research, documentation, and communication. These analysts often work for federal agencies, advocacy organizations, and research institutions.
Key Responsibilities
The primary tasks include researching legislation and industry standards to ensure compliance, gathering feedback from stakeholders, and simplifying complex legal or technical requirements into clear policies. Analysts also review internal procedures and suggest improvements to reduce risk. On average, the annual base salary for this role is approximately $116,776.
This research-intensive position provides a strong foundation for advancing into higher-level cybersecurity governance roles.
Relevance for Beginners
This role is ideal for those transitioning into cybersecurity who excel at managing processes and people rather than diving into technical engineering. Degrees in fields like political science, international relations, law, social policy, or psychology are highly regarded. Entry-level certifications, such as CompTIA Security+ or ISC2 Certified in Cybersecurity (CC), can further demonstrate basic security knowledge.
Potential Career Growth
Starting as a Policy Analyst can lead to senior roles in governance, risk, and compliance management, where professionals develop and oversee risk strategies. With the cybersecurity sector expected to grow by 33% between 2023 and 2033, there’s plenty of room for advancement. With experience, analysts can move into positions like Data Protection Officer, Cybersecurity Manager, or even Chief Information Security Officer (CISO).
6. IT Security Auditor
Job Description
An IT Security Auditor plays a crucial role in safeguarding an organization's network and data. Instead of diving into technical fixes, auditors focus on identifying cybersecurity gaps, communicating potential risks to leadership, and ensuring compliance with regulations like Sarbanes-Oxley (SOX) and standards such as SOC-2 or PCI-DSS. Walter Ford, IT Manager at Keeper Security, highlights the role's focus:
"An auditor does not necessarily need to be highly technical, but it does help. They do need critical thinking skills to determine whether a control is covered by the company's processes."
Key Responsibilities
The job revolves around evaluating current security practices and ensuring they meet regulatory standards. IT Security Auditors design and conduct audits, whether for specific departments or the entire organization, and review system logs to detect security breaches. They compile detailed reports, often including cost–benefit analyses for suggested improvements, and create policies to align with compliance requirements.
In the U.S., IT Security Auditors typically earn around $111,400 annually, with more than 7,600 job openings available. For comparison, the median salary for information security analysts is $124,910. Practical audits conducted by these professionals have led to noticeable improvements in organizational security.
Relevance for Beginners
This role is considered an entry point into the cybersecurity field, making it accessible to those without advanced technical skills or coding knowledge. Success in this position requires strong critical thinking, attention to detail, and an understanding of business operations. Many IT Security Auditors come from backgrounds in IT support, network administration, or risk analysis. To stand out, beginners can pursue certifications like Certified Information Systems Auditor (CISA), CompTIA Security+, or IT Infrastructure Library (ITIL).
Potential Career Growth
Starting as an IT Security Auditor can open doors to higher-level positions, such as Senior Cybersecurity Auditor, Cybersecurity Consultant, Risk Management Specialist, or Information Security Manager. Over time, professionals in this field can aim for executive roles like Chief Information Security Officer (CISO).
The demand for information security analysts is expected to grow by 29% between 2024 and 2034. For entry-level auditors, salaries start at about $58,616 annually, while those with significant experience can earn up to $172,000.
sbb-itb-8a31326
7. Security Operations Technician
Job Description
A Security Operations Technician plays a crucial role in safeguarding an organization's cybersecurity framework. These professionals are tasked with monitoring, analyzing, and responding to potential threats as they happen. Erika McDuffie, Senior Director at Coalfire, describes the importance of this role:
"Entry-level SOC analysts are the 'front line' of defense for an organization. This role is designed to provide a human element to support the tooling and sensors leveraged by organizations."
The job revolves around keeping a close eye on security alert queues and using SIEM (Security Information and Event Management) tools to identify suspicious activity. Acting as triage experts, technicians determine whether alerts signal real threats or are simply false positives. Major issues are then escalated to senior analysts for further investigation. These responsibilities form the backbone of their daily work.
Key Responsibilities
A Security Operations Technician’s daily duties focus on monitoring and maintaining security systems. This includes reviewing security logs, ensuring backup systems and sensors are operational, investigating incidents from detection through resolution while documenting each step, and collaborating with IT teams to manage user accounts and access permissions.
Starting salaries for entry-level technicians generally range from $55,000 to $75,000 per year, while the median salary for cybersecurity professionals is approximately $98,300.
Relevance for Beginners
This role is an excellent starting point for those new to cybersecurity. It emphasizes monitoring and incident triage rather than advanced technical skills. David Forsythe, Training Lab Architect at Hack The Box, highlights its accessibility:
"SOC is the most accessible entry-level position, as there are tons of positions out there. Even at the most entry-level position, you get hands-on experience triaging alerts, understanding false positives and what causes them."
The job doesn’t require extensive coding knowledge but instead values critical thinking and basic technical skills. Beginners can strengthen their qualifications by earning certifications like CompTIA Security+ or CySA+ and gaining hands-on experience in networking basics, as well as Linux and Windows administration.
Potential Career Growth
Starting in this role can open doors to mid-level positions, such as Incident Responder, Threat Intelligence Analyst, or Security Engineer, within just a few years. These roles typically pay between $90,000 and $120,000 annually. Over time, professionals can aim for leadership roles like Security Architect or Chief Information Security Officer (CISO), where salaries often exceed $150,000.
Gary Ruddell, Head of Cyber Threat Intelligence, underscores the value of gaining experience in a SOC role:
"There's no better way to learn cybersecurity than spending time in the trenches on the front lines. That's what the SOC is... From there, you can go anywhere."
Moreover, the demand for information security analysts is expected to grow by 29% to 31% over the next decade, reflecting the increasing importance of cybersecurity expertise in today’s digital landscape.
8. Junior Security Consultant
Job Description
A Junior Security Consultant helps organizations improve their security measures. Instead of being part of an internal security team, these consultants often work with external firms, assisting clients from various industries. Their job involves spotting security weaknesses, suggesting solutions, and ensuring that companies meet industry standards.
They also act as a bridge between technical teams and business leaders, translating complex security risks into clear, actionable advice for non-technical stakeholders. Under the guidance of senior colleagues, they conduct risk assessments and help clients align their cybersecurity practices with regulatory frameworks like NIST, ISO 27001, GDPR, or HIPAA.
Key Responsibilities
Junior Security Consultants focus on identifying vulnerabilities through risk assessments and evaluating their potential impact. They document their findings and translate technical details into straightforward recommendations for decision-makers. Additionally, they review and draft internal security policies to ensure compliance with regulations. Client collaboration is a significant part of the role, as consultants work with both technical teams and management to implement security improvements and maintain compliance.
Relevance for Beginners
For newcomers to cybersecurity, this role is an excellent starting point, especially for those without an extensive technical background. As experts explain:
Cybersecurity is a multidisciplinary field requiring a mix of technical and soft skills, depending on the role.
This position is particularly suitable for individuals with experience in business, law, auditing, or project management. Strong communication, problem-solving, and attention to detail - skills that can transfer from other fields - are essential. While not mandatory, IT or cybersecurity certifications are highly regarded by employers. Beginners can boost their credentials by earning certifications like CompTIA Security+ or ISC2 SSCP. The role also provides exposure to security practices across industries such as finance, healthcare, and government, offering a broad understanding of diverse security challenges.
Potential Career Growth
Starting as a Junior Security Consultant can lead to higher-paying roles as you gain experience. For instance, cyber risk analysts with 1–3 years of experience earn an average salary of about $114,000. With more experience, opportunities open up for roles like Security Architect (average salary: $164,433), Cybersecurity Manager ($153,084), or Security Engineer ($137,879). The cybersecurity industry is expected to grow by 33% between 2023 and 2033, reflecting the increasing demand for skilled professionals. Consulting experience builds a strong foundation in understanding both business processes and security controls, which can be valuable when transitioning into specialized or leadership roles. Next, we’ll look at roles that blend customer service with technical support.
9. Cybersecurity Help Desk Specialist
Job Description
A Cybersecurity Help Desk Specialist acts as the first line of defense for addressing security-related issues within an organization. Whether through phone calls, emails, or ticketing systems, they respond to requests and resolve - or escalate - problems efficiently. Common tasks include managing password resets and account unlocks to prevent unauthorized access. They also assist users by installing and configuring security software, troubleshooting security-related hardware or software issues, and documenting incidents for further review.
Kristoffer Marshall from CompTIA highlights the importance of this role:
All of the tech know-how in the world doesn't matter if you can't effectively communicate the hows and whys of cybersecurity to the true first line of defense - the person sitting at a keyboard with something to lose.
Key Responsibilities
Daily responsibilities revolve around triaging security requests and resolving issues related to operating systems, networks, and security configurations. Specialists maintain detailed records by updating internal knowledge bases and keeping thorough ticket logs. They also serve as a bridge between technical teams and end users, ensuring security policies are explained in a clear and accessible way. Another critical aspect of the job is understanding how security measures impact business operations. For instance, knowing when shutting down a compromised server might disrupt essential processes. These experiences not only strengthen technical skills but also prepare specialists for more advanced roles in cybersecurity. In many organizations, the help desk works closely with the Security Operations Center (SOC), contributing to a more cohesive security strategy.
Relevance for Beginners
This role is an excellent entry point for anyone starting a cybersecurity career without a deep technical background. IT Support Specialists earn an average salary of about $53,221, while those advancing to incident analyst roles typically earn between $64,000 and $70,000. Foundational certifications like CompTIA A+ or Security+ are highly recommended for those pursuing this path.
Kristoffer Marshall shares his perspective on the help desk experience:
The help desk is a stepping stone to a different path. I learned more in my year working the help desk than I did the rest of my 12-year career.
This role not only builds technical troubleshooting skills but also hones soft skills, such as calming frustrated users and explaining complex concepts in simple terms. These abilities are invaluable as you progress in cybersecurity. With only 82 cybersecurity professionals available for every 100 open positions in the U.S., the demand for help desk specialists creates significant opportunities for newcomers.
For more resources on starting your cybersecurity journey, check out Root School.
Potential Career Growth
Starting at the help desk opens the door to numerous career paths in cybersecurity. Many professionals transition into roles like SOC Analyst, Security Administrator, or Junior Digital Forensics Analyst. The skills gained - ranging from understanding system functionality to effectively communicating security concepts - are directly applicable to these advanced roles. Cybersecurity jobs are expected to grow by 29% between 2024 and 2034, offering plenty of room for advancement. With additional certifications and technical expertise, you could move into mid-level positions such as Penetration Tester or Security Engineer. Over time, experienced professionals often step into senior roles like Security Architect (average salary: $164,433) or Cybersecurity Manager (average salary: $153,084). The help desk experience provides a unique blend of technical and interpersonal skills that remain valuable throughout a cybersecurity career.
10. Forensic Report Analyst
Job Description
A Forensic Report Analyst dives into the aftermath of cyber incidents, piecing together the digital puzzle to uncover how breaches occurred and who was behind them. Unlike roles that focus on preventing attacks, this position zeroes in on post-incident investigations. Analysts retrieve and analyze data from devices like computers and smartphones to reconstruct events and provide clarity to legal teams, law enforcement, or corporate stakeholders.
For example, in November 2025, EY (Ernst & Young) advertised a "Cyber Triage and Forensics – Junior Analyst" position in Hoboken, NJ. This role involves real-time monitoring, log analysis, and active participation in investigations. The salary for this entry-level position ranges from $72,500 to $124,500.
Key Responsibilities
Forensic Report Analysts are tasked with collecting, preserving, and analyzing digital evidence while maintaining a strict chain of custody to ensure it holds up in legal proceedings. They recover data from erased or damaged devices, decode metadata, rebuild timelines of unauthorized access, and compile technical findings into reports that non-technical audiences can understand. Additionally, they may testify as expert witnesses in court or assist law enforcement in criminal cases.
"The CTF [Cyber Triage and Forensics] Analyst I must be competent to work at a technical level, be capable of identifying threats and vectors that cause security events and be able to follow defined procedures for mitigating said threats." - EY Careers
Relevance for Beginners
This role is beginner-friendly and doesn’t require an advanced technical background. It’s particularly suited for individuals with a foundation in criminal justice or those with a knack for detailed analysis and critical thinking. The job relies more on investigative and reporting skills than deep technical expertise, making it a great entry point for non-technical professionals. Junior Forensic Analysts typically earn between $70,000 and $90,000 annually, while experienced Digital Forensic Examiners average around $96,157.
The field is growing rapidly. The global digital forensics market is expected to expand from $13.2 billion in 2024 to $15 billion in 2025, and jobs for information security analysts are projected to grow by 33% between 2023 and 2033. Certifications like GIAC Certified Forensic Analyst (GCFA), Certified Computer Examiner (CCE), and EnCase Certified Examiner (EnCE) enhance credibility and validate skills. Degrees in Criminal Justice, Law, or Business, along with strong technical writing abilities, can also boost your qualifications.
Potential Career Growth
Starting as a Forensic Report Analyst opens doors to higher-level roles like Incident Response Lead, Security Architect, or even Chief Information Security Officer (CISO). Career progression often follows a path from Junior Analyst to Senior Analyst, then to Security Operations Center (SOC) Manager, and ultimately executive positions. With experience, analysts can transition into consulting roles, advising organizations on risk management and incident response strategies. The expertise gained - ranging from evidence handling to breaking down technical findings for diverse audiences - remains valuable throughout a cybersecurity career. This role offers a solid foundation for advancing into leadership positions in the field.
6 Cybersecurity Jobs with ZERO Tech Skills
Conclusion
Non-technical cybersecurity careers are more accessible than you might think. With a global shortage of 4.8 million professionals in the field and 25% of U.S. vacancies centered on oversight and governance roles, there's a clear demand for non-technical expertise. As the cybersecurity industry continues to expand, now is an opportune moment to dive in.
Here's the bottom line: You don’t need coding skills to make a meaningful impact in cybersecurity. Many roles draw on skills you may already possess, like communication, critical thinking, project management, or legal knowledge. Considering that over 90% of security breaches are linked to human error, organizations are eager to hire professionals who can tackle the human side of cybersecurity.
To get started, focus on identifying your transferable skills and pursuing certifications like CompTIA Security+ or the Google Cybersecurity Professional Certificate. While job postings might mention experience, 87% of employers prioritize certifications and proven skills. Resources like Root School (https://root-school.com) can help you build a strong portfolio and prepare for interviews, making your entry into the field smoother.
Cybersecurity is actively seeking diverse talent, and your first step could lead to a rewarding, high-paying career.
FAQs
What are the best certifications for starting a non-technical career in cybersecurity?
For those aiming for non-technical roles in cybersecurity, CompTIA Security+ stands out as a key certification. Employers often see it as a solid indicator of foundational skills in areas like risk management, compliance, and security policies. Professionals starting out with this certification can expect competitive pay, with average salaries reaching about $86,885 per year.
There are also other certifications that can enhance your career opportunities. Credentials from organizations such as (ISC)² or ISACA, which focus on governance, compliance, and security awareness, are highly regarded. These certifications highlight your readiness for roles centered on policy development, training, and risk assessment - making them a strong choice for individuals without a technical background.
How can someone with a legal background start a career in cybersecurity?
A legal background can be a powerful advantage when stepping into non-technical roles within cybersecurity. Skills like interpreting regulations, evaluating risks, and explaining complex concepts are highly valued. Entry-level positions such as security compliance analyst, privacy officer, cyber policy analyst, or legal counsel for information security provide opportunities to apply your legal expertise to areas like data privacy laws and regulatory compliance.
To make the shift, start by identifying your transferable skills - things like contract review or risk assessment - and pair them with a foundational understanding of cybersecurity. Online courses are a great way to get started. Adding certifications such as CIPP/US, CISA, or CompTIA Security+ to your resume can also help establish your credibility and make it easier to collaborate with technical teams. Gaining hands-on experience, like contributing to compliance projects or drafting policies, can further boost your qualifications.
Building a network is another key step. Engage with cybersecurity professionals, join organizations like ISACA or IAPP, and seek mentorship opportunities to gain insights and guidance. Platforms like Root School offer free resources and beginner-friendly courses designed to help those with legal expertise transition smoothly into cybersecurity roles.
What skills do you need to succeed in non-technical cybersecurity roles?
Success in non-technical cybersecurity roles hinges more on people skills and process-driven abilities than on deep technical knowledge. Being able to communicate clearly - whether in writing or speaking - is a must. This includes breaking down complex security ideas for non-technical audiences, creating training materials, or crafting policies that are easy to follow. Equally important are critical thinking and analytical skills, which help in assessing risks, spotting vulnerabilities, and making sound decisions.
Skills like project management and staying organized are crucial, especially for positions that require managing security initiatives or ensuring compliance with regulations. Understanding risk management frameworks and industry standards such as GDPR, HIPAA, or NIST can give candidates an edge, particularly in governance, risk, and compliance (GRC) roles. Those who pay attention to detail, learn proactively, and solve problems efficiently often thrive by acting as a bridge between technical teams and business stakeholders.


