Threat intelligence analysts need specialized certifications to stand out in cybersecurity. These certifications validate skills in analyzing threats, understanding adversary tactics, and improving organizational defenses. Top certifications include:
- CTIA (Certified Threat Intelligence Analyst): Hands-on focus on the threat intelligence lifecycle, Python scripting, and practical labs.
- GCTI (GIAC Cyber Threat Intelligence): Advanced threat analysis, frameworks like MITRE ATT&CK, and professional-grade reporting.
- CySA+ (CompTIA Cybersecurity Analyst): Early-career credential emphasizing detection, response, and analytics.
- CISSP (Certified Information Systems Security Professional): Broad security expertise for senior-level roles.
- SANS FOR508: Advanced training in threat hunting and incident response.
Certifications like CTIA and GCTI are ideal for specialized roles, while CISSP prepares professionals for leadership. CySA+ is a solid starting point for beginners. Choose based on your career stage and goals.
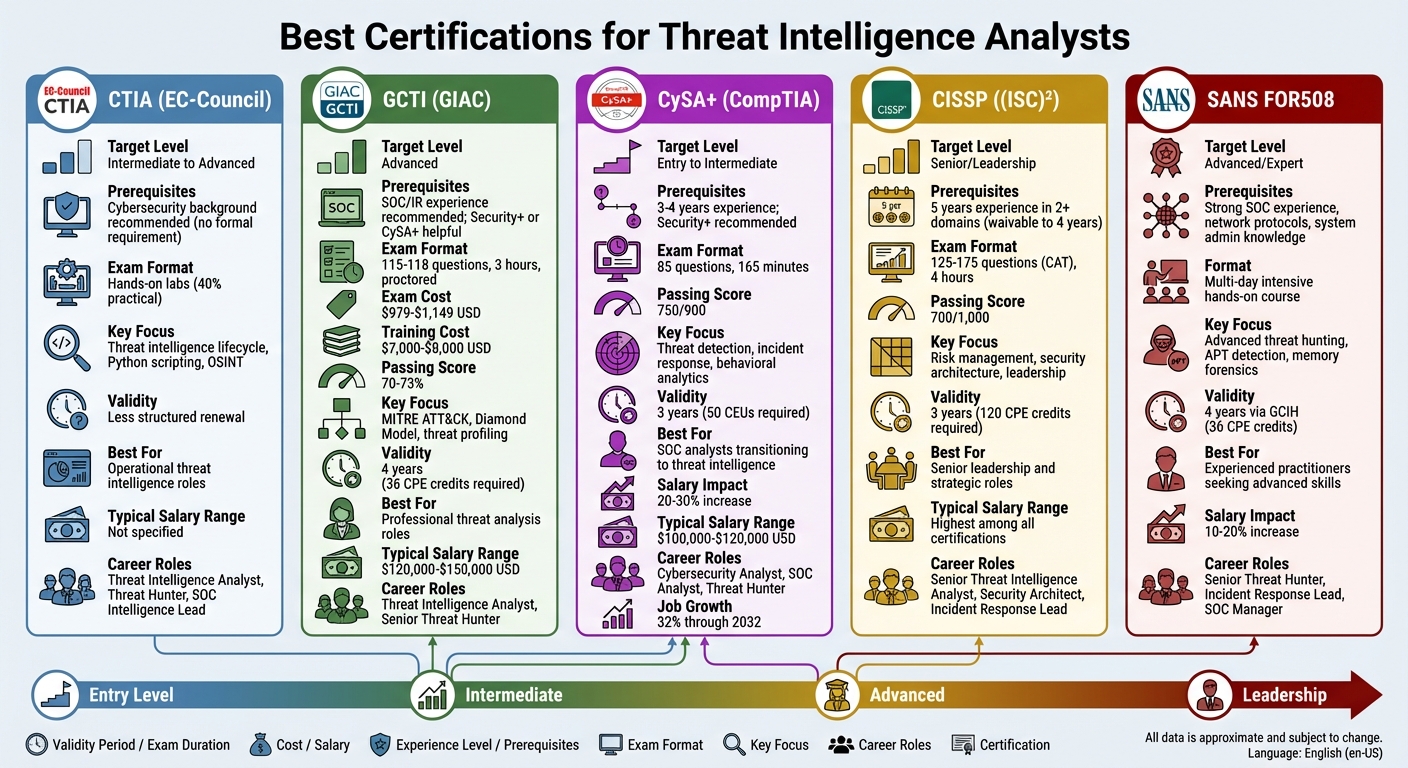
Comparison of Top 5 Threat Intelligence Analyst Certifications
EC-Council CTIA v2 Certification: Complete 2025 Guide to Becoming a Threat Intelligence Analyst

1. EC-Council Certified Threat Intelligence Analyst (CTIA)
The EC-Council Certified Threat Intelligence Analyst (CTIA) certification is designed for professionals aiming to master the entire threat intelligence lifecycle - spanning planning, collection, analysis, production, and dissemination. With 40% of the program dedicated to hands-on labs, participants work through real-world scenarios to build practical expertise. This mix of theory and application is ideal for analysts transitioning from basic alert monitoring to more advanced, proactive roles in threat intelligence.
Prerequisites
While there are no strict formal prerequisites, the CTIA certification is best suited for individuals with a cybersecurity background. Familiarity with networking basics or security operations is helpful. Professionals moving from roles like SOC analyst or incident responder will find their existing knowledge of cybersecurity valuable when pursuing this certification.
Exam Format
The CTIA exam is part of a structured training program that emphasizes both theoretical and practical learning. The curriculum includes hands-on labs where candidates practice tasks such as gathering threat data using OSINT tools, automating processes with Python, and developing detailed threat intelligence reports. Although specific exam details are not disclosed, the test evaluates your ability to apply skills across all stages of the threat intelligence lifecycle.
Core Topics
The certification covers a broad range of topics, including strategic, operational, tactical, and technical intelligence. Participants work with frameworks like MITRE ATT&CK, the Cyber Kill Chain, and the Diamond Model to track threat actors and advanced persistent threats. Key areas of focus include:
- Data collection methods such as OSINT and HUMINT.
- Identifying indicators of compromise (IOCs).
- Analytical techniques like Statistical Data Analysis and Structured Analytic Techniques.
- Python scripting for automating threat hunting efforts.
- Integrating threat intelligence into SOC operations, incident response, and risk management.
Career Impact
Obtaining the CTIA certification can open doors to roles like threat intelligence analyst, threat hunter, or SOC intelligence lead. The program’s emphasis on Python automation and hands-on report writing equips you with actionable skills that stand out in job interviews. In the competitive U.S. cybersecurity job market, where employers value professionals who can go beyond basic alert triage to implement proactive defense strategies, this certification highlights your ability to make a meaningful impact.
2. GIAC Cyber Threat Intelligence (GCTI)

The GIAC Cyber Threat Intelligence (GCTI) certification is closely tied to the SANS FOR578 course and is designed for those deeply involved in threat analysis. It demonstrates your ability to handle every stage of the threat intelligence lifecycle, from gathering and analyzing threat data to creating actionable reports that guide critical security decisions. Unlike general security certifications, GCTI zeroes in on defender-focused intelligence, leveraging tools like the MITRE ATT&CK framework and the Diamond Model to enhance threat analysis skills.
Prerequisites
While GIAC doesn’t impose formal prerequisites, candidates often benefit from experience in roles like security operations, incident response, or security analysis. Familiarity with logs, network artifacts, and attacker behaviors can make a big difference. Many professionals pursuing GCTI already hold foundational certifications such as CompTIA Security+ or CySA+ and work as SOC analysts or incident responders. This prior knowledge provides a strong base for tackling the exam and coursework.
Exam Format
The GCTI exam features 115–118 multiple-choice and scenario-based questions. It’s a proctored, closed-book test that lasts 3 hours. The exam fee ranges from $979 to $1,149 USD. To prepare, many candidates take the SANS FOR578 training course, which costs between $7,000 and $8,000 USD and includes an exam voucher. To pass, you’ll typically need a score between 70% and 73%.
Core Topics
The GCTI curriculum dives into the critical elements of cyber threat intelligence. You’ll explore frameworks for intrusion analysis, learn to build detailed threat profiles, and produce various intelligence products. The program also emphasizes evaluating external threat feeds, sharing intelligence, and creating reports tailored for different audiences - from executive summaries to tactical indicators for security teams. These skills are applied to classify adversary techniques using established frameworks.
Validity and Renewal
The certification remains valid for 4 years. To renew, you’ll need to earn 36 Continuing Professional Education (CPE) credits through approved activities and pay a renewal fee. This process ensures that certified professionals stay updated on emerging threats and analysis methods.
Career Impact
Holding a GCTI certification can significantly boost your career opportunities, particularly with employers like financial institutions, tech firms, defense contractors, and Managed Security Service Providers (MSSPs). In the U.S., positions such as Threat Intelligence Analyst and Senior Threat Hunter often list GIAC or SANS CTI certifications as preferred qualifications. Salary data shows that professionals with GCTI certification typically earn between $120,000 and $150,000 USD annually. Paired with hands-on experience, this certification can also lead to consulting roles focused on developing or refining threat intelligence programs.
3. CompTIA Cyber Security Analyst (CySA+)

The CompTIA CySA+ certification serves as a practical step for those looking to advance from foundational cybersecurity skills to proactive threat detection. Positioned after advanced certifications like CTIA and GCTI, CySA+ focuses on behavioral analytics, threat detection, and incident response, making it a valuable credential for professionals aiming to work as SOC analysts, threat hunters, or transition into threat intelligence roles.
Prerequisites
CompTIA suggests that candidates pursuing CySA+ have 3–4 years of hands-on experience in security or related fields. A foundational certification like Security+ is highly recommended, as it prepares candidates for the exam's emphasis on analytics and threat detection.
Exam Format
The CySA+ exam (code CS0-003) includes up to 85 multiple-choice and performance-based questions. You’ll have 165 minutes to complete the test, and a passing score is 750 out of 900. Performance-based questions mirror real-world scenarios, such as identifying anomalies in network traffic or analyzing indicators of compromise. This hands-on approach aligns closely with the skills required for threat intelligence roles, ensuring its relevance in the U.S. cybersecurity job market.
Core Topics
The CySA+ curriculum covers key areas:
- Threat and vulnerability management
- Security operations and monitoring
- Incident response
- Compliance reporting
It also delves into IoC (Indicators of Compromise) analysis, threat hunting with SIEM/EDR tools, and applying industry frameworks. Additionally, there’s a focus on scripting - particularly Python - to automate tasks like threat hunting and streamline SOC workflows.
Validity and Renewal
The certification is valid for 3 years. To renew it, you’ll need to earn 50 Continuing Education Units (CEUs) through activities like training, attending conferences, or obtaining higher certifications such as CASP+. Alternatively, you can retake the exam. Keeping your CySA+ certification current ensures your skills stay relevant and supports long-term career growth.
Career Impact
Earning a CySA+ certification can boost salaries by 20–30% in cybersecurity roles. In the U.S., professionals such as cybersecurity analysts, SOC analysts, or threat hunters often earn between $100,000 and $120,000 annually. The U.S. Bureau of Labor Statistics predicts a 32% growth in information security analyst roles through 2032, with over 70% of SOC roles by 2025 expected to require analytics-focused certifications like CySA+. This certification validates critical analytical skills and positions you for success in the competitive field of threat intelligence.
While certifications like CTIA and GCTI emphasize deeper threat intelligence analysis, CySA+ hones operational response and detection skills - key for tackling today’s cybersecurity challenges.
4. Certified Information Systems Security Professional (CISSP)
The CISSP certification, offered by (ISC)², takes your cybersecurity expertise to the next level by focusing on strategic leadership and a broad understanding of security principles. Unlike niche certifications such as CTIA and GCTI, which emphasize hands-on threat intelligence techniques, CISSP validates your knowledge in areas like risk management, asset classification, secure architecture, and security operations. These skills are essential for senior-level roles in threat intelligence and broader cybersecurity leadership.
Prerequisites
To qualify for the CISSP certification, you need at least five years of full-time work experience in two or more of the eight CISSP domains. If you have a four-year college degree or hold a qualifying credential, one year of this requirement can be waived. Relevant roles include SOC analyst, incident responder, security engineer, or security consultant. For those who don’t yet meet the experience requirement, there’s an alternative: pass the exam to become an Associate of (ISC)² and gain the necessary experience over time. This route is especially helpful for early-career professionals leveraging Root School training to build both theoretical knowledge and hands-on skills. It’s a great way to validate your expertise while preparing for leadership positions in cybersecurity.
Exam Format
The CISSP exam uses a Computerized Adaptive Testing (CAT) format and includes 125–175 questions to be completed within 4 hours. Most questions are multiple-choice, but some may involve drag-and-drop or scenario-based formats. The scoring ranges from 100 to 1,000, and you’ll need a score of 700 or higher to pass. U.S.-based candidates can take the exam at Pearson VUE testing centers or through approved online proctoring.
Core Topics
CISSP spans eight domains as part of the (ISC)² Common Body of Knowledge. However, for threat intelligence professionals, four domains offer the most direct value:
- Security and Risk Management: Topics like threat modeling, risk prioritization, and assessing business impact.
- Communication and Network Security: Focus on network architectures, protocols, and identifying attack paths.
- Security Operations: Covers incident response and effective logging practices.
- Security Assessment and Testing: Involves validating defenses and fine-tuning detection rules.
These areas help you align threat intelligence efforts with overarching security strategies and risk management goals.
Validity and Renewal
The CISSP certification remains valid for three years. To maintain it, you’ll need to earn 120 Continuing Professional Education (CPE) credits during the three-year cycle and pay an Annual Maintenance Fee (AMF). CPE credits can be earned through activities like attending conferences, publishing research, completing advanced training, presenting at industry events, or documented self-study. With the fast-paced changes in threat intelligence, tasks like researching new APT campaigns or exploring emerging frameworks can also contribute toward your CPE requirements. This ensures that your knowledge stays current and complements specialized threat intelligence certifications by broadening your overall security expertise.
Career Impact
CISSP is one of the most sought-after and highly compensated cybersecurity certifications in the U.S. Job postings for roles such as Senior Threat Intelligence Analyst, Threat Hunter, Incident Response Lead, and Security Architect often list CISSP as a preferred qualification. Professionals with this certification tend to earn higher salaries, reflecting the advanced knowledge and leadership skills it represents. By earning the CISSP credential, you can set yourself apart for roles that require integrating threat intelligence with risk management, secure architecture, and governance.
While certifications like CTIA and GCTI specialize in deep threat intelligence skills, CISSP equips you for leadership roles that connect intelligence efforts with broader business goals and security strategies.
sbb-itb-8a31326
5. SANS FOR508: Advanced Incident Response and Threat Hunting

SANS FOR508 delivers an immersive, hands-on experience in advanced threat hunting and incident response. Unlike certifications that center around exams, this course prioritizes practical expertise in detecting and neutralizing advanced persistent threats (APTs) designed to slip past standard defenses. It's tailored for professionals looking to shift from reactive security measures to proactive threat-hunting strategies.
Prerequisites
This course is ideal for those with a solid foundation in cybersecurity, experience in Security Operations Centers (SOC), and familiarity with network protocols, system administration, and security principles. SANS recommends having this background before enrolling. If you've completed Root School training and gained practical experience in security operations, you'll likely be well-prepared for the advanced concepts in FOR508. Root School training complements this course by bridging basic security operations with advanced threat-hunting techniques.
Core Topics
FOR508 focuses on hypothesis-driven threat hunting using frameworks like MITRE ATT&CK. The course includes intensive labs covering memory forensics (such as investigating malware like Cobalt Strike), pivoting techniques for tracking APT infrastructures, and network analysis for detecting post-exploitation activity. Real-world scenarios include hunting ransomware operators and identifying attacks that bypass traditional defenses. By the end of the course, you'll be equipped to analyze attacker behavior patterns and neutralize threats before they escalate.
Validity and Renewal
The course aligns with the GIAC Certified Incident Handler (GCIH) certification, which remains valid for four years. To renew your credential, you'll need to earn 36 Continuing Professional Education (CPE) credits through activities like attending training, participating in conferences, or publishing research. Alternatively, you can retake the certification exam. This renewal process ensures your skills keep pace with the evolving cyber threat landscape.
Career Impact
Graduates of FOR508 are well-prepared for roles such as Senior Threat Hunter, Incident Response Lead, or SOC Manager. Employers value the course for its focus on practical, real-world threat detection. Professionals who complete this training often see salary increases ranging from 10–20% and may step into leadership roles within threat intelligence teams. As organizations increasingly emphasize proactive threat hunting over reactive responses, the advanced skills gained through FOR508 are becoming indispensable for career advancement in cybersecurity.
Pros and Cons
Choosing the right certification in threat intelligence depends on understanding what each one brings to the table - and where it might fall short. Here's a closer look at how these certifications stack up.
CTIA stands out for its practical, hands-on approach, with 40% of its curriculum dedicated to lab work. These labs simulate real-world threat intelligence scenarios, making it a solid choice for those in operational roles.
GCTI provides a well-rounded focus on strategic, operational, and tactical intelligence. Its rigorous proctored exam format ensures a deep understanding of the field, and it’s widely regarded as a respected certification in threat intelligence.
CySA+ serves as an entry-level credential, typically requiring 3–4 years of experience or foundational certifications like Security+. It’s great for building skills in threat detection and incident response, but it doesn’t dive as deeply into advanced threat-hunting techniques as some specialized certifications.
CISSP is designed for professionals with 5+ years of experience across various security domains. Aimed at those pursuing senior roles, it features a challenging 250-question adaptive exam and requires renewal every three years with the completion of 120 CPE credits. This certification focuses on broad, high-level security expertise.
FOR508 zeroes in on advanced threat hunting and incident response. Its intensive, multi-day format makes it ideal for seasoned practitioners looking to sharpen their expertise.
When it comes to renewal, the timelines vary. GIAC certifications, like GCTI, require renewal every four years, while CySA+ and CISSP need to be renewed every three years. CTIA’s renewal process is less structured, which might be a factor for those prioritizing long-term credential upkeep.
The career impact of these certifications also depends on your goals. CTIA and GCTI are tailored for dedicated threat intelligence roles. CySA+ lays the groundwork for work in security operations centers and entry-level threat hunting. CISSP is highly regarded for advancing into leadership positions, while FOR508 equips experienced professionals with advanced skills for tackling complex incident response scenarios.
How to Prepare for Certification Exams
Once you understand the advantages and challenges of certifications, it's time to focus on a targeted study plan that aligns with your goals.
Start by reviewing the exam objectives for your chosen certification and creating a study schedule. For candidates in the U.S. who are juggling full-time jobs, aim to dedicate 8–10 hours per week for 8–12 weeks per certification. Break this into manageable 60–90 minute study sessions on weeknights, saving longer hands-on lab work for weekends.
Practical experience is especially important for certifications like CTIA, GCTI, CySA+, and FOR508, which emphasize applied skills. You can set up a budget-friendly home lab using virtual machines to mimic real-world enterprise environments. Use this lab to practice tasks like OSINT collection, analyzing malware samples or PCAP files for indicators, and exploring open-source SIEM or EDR tools to track adversary behavior. For CTIA, focus on mastering the threat intelligence lifecycle and basic Python scripting. FOR508 candidates should meticulously document every step of their processes to build strong analytical habits.
Incorporate key frameworks such as MITRE ATT&CK, the Cyber Kill Chain, and the Diamond Model into your daily practice. For each case study you analyze, map the adversary's behavior to ATT&CK tactics and techniques, align their actions with the Kill Chain, and model intrusions using the Diamond Model. Keeping a personal "framework notebook" with detailed examples and diagrams can be a valuable resource for both learning and last-minute review. Additionally, U.S.-based learners should consider studying publicly available reports from government agencies or ISACs to understand professional analytic standards. These activities help solidify the analytical skills that are critical for passing the exams.
Be sure to familiarize yourself with the continuing education requirements for each certification and plan for the long term. For example, CISSP and GIAC certifications require earning a specific number of continuing professional education (CPE) credits every three years. These credits can be earned through conferences, courses, publications, or even teaching in the U.S.. Keep track of your CPE activities to ensure you meet renewal requirements. If you’re just starting out in cybersecurity, platforms like Root School offer structured labs and resources tailored to entry- and mid-level certifications.
Finally, take timed, full-length practice tests to identify and eliminate common distractor answers. If your exam is proctored - whether at a U.S. testing center or online - conduct a technical rehearsal a few days before to ensure your setup is ready. Solid preparation not only boosts your chances of certification success but also sharpens the skills you'll rely on as a threat intelligence analyst.
Conclusion
The certifications discussed above cater to a range of experience levels and career aspirations. Selecting the right certification depends on where you are in your career and the role you aim to achieve.
For those just starting out, CompTIA CySA+ offers a great foundation. It focuses on threat detection and incident response skills without requiring prior certifications, making it an excellent choice for landing your first SOC analyst position.
If you're progressing into threat intelligence, certifications like CTIA and GCTI are key steps forward. CTIA covers the entire threat intelligence lifecycle, including approximately 40% hands-on labs and Python scripting, preparing you for roles such as threat hunter or SOC lead. GCTI, on the other hand, is highly regarded worldwide and is ideal for analysts with a solid understanding of security fundamentals who want to enhance their skills in adversary tracking and analytic tradecraft.
For seasoned professionals, CISSP and SANS FOR508 address different career paths. CISSP validates expertise across eight security domains and is tailored for senior roles like security managers or architects. Meanwhile, SANS FOR508 focuses on advanced incident response and threat hunting, equipping experts to lead investigations and counter persistent threats. Together, these certifications support growth from operational roles to strategic leadership positions.
A typical career path might begin with CySA+ to build foundational skills, move to CTIA or GCTI for specialization in threat intelligence, and ultimately lead to CISSP for leadership roles. If you're just starting your cybersecurity journey, platforms like Root School can help you develop practical skills and job-search strategies to kickstart your career.
FAQs
What are the benefits of earning a CTIA certification for your cybersecurity career?
Earning a CTIA certification can be a game-changer for your cybersecurity career. It showcases your expertise in threat intelligence, adding a layer of credibility to your professional profile and positioning you as a strong contender for specialized roles.
This certification doesn’t just validate your skills - it can also expand your job prospects and potentially increase your earning potential. Employers tend to prioritize certified candidates because it signals proven knowledge and capability, helping you stand out in a crowded and competitive field.
What are the key differences between the GCTI and CySA+ certifications in focus and career opportunities?
The GCTI (GIAC Cyber Threat Intelligence) certification is designed for professionals who focus on threat intelligence. It hones in on skills like threat research, intelligence gathering, and analysis, making it a great fit for roles dedicated to understanding and tackling advanced cyber threats.
Meanwhile, the CySA+ (CompTIA Cybersecurity Analyst) certification offers a broader overview of cybersecurity. It covers key areas such as vulnerability management, incident response, and security monitoring, making it a solid choice for a variety of cybersecurity roles.
For those pursuing a specialized path in threat intelligence, GCTI provides a more focused approach. On the other hand, CySA+ serves as a flexible option for individuals seeking a well-rounded foundation in cybersecurity.
What certifications are best for advancing to a leadership role in cybersecurity?
If you're setting your sights on a leadership role in cybersecurity, two certifications stand out: CISSP (Certified Information Systems Security Professional) and CISA (Certified Information Systems Auditor).
The CISSP is tailored for professionals looking to showcase their skills in designing and managing security programs across an organization. It's a strong fit for those aiming to lead enterprise-level security initiatives. Meanwhile, the CISA is geared toward individuals focused on auditing, controlling, and maintaining the integrity of IT systems. This certification is particularly valuable for roles centered on governance and compliance.
Both certifications hold a strong reputation in the industry and can open doors to advanced leadership opportunities.