Threat intelligence helps you understand and respond to cyber threats by identifying attackers, their tools, and goals. Starting at home is easier than you think. With basic equipment like a mid-range computer, free tools, and virtual machines (VMs), you can build a home lab to gain hands-on cybersecurity skills. This guide covers:
- Setting up a home lab: Use VirtualBox to create safe, isolated environments with Linux and Windows VMs for analysis.
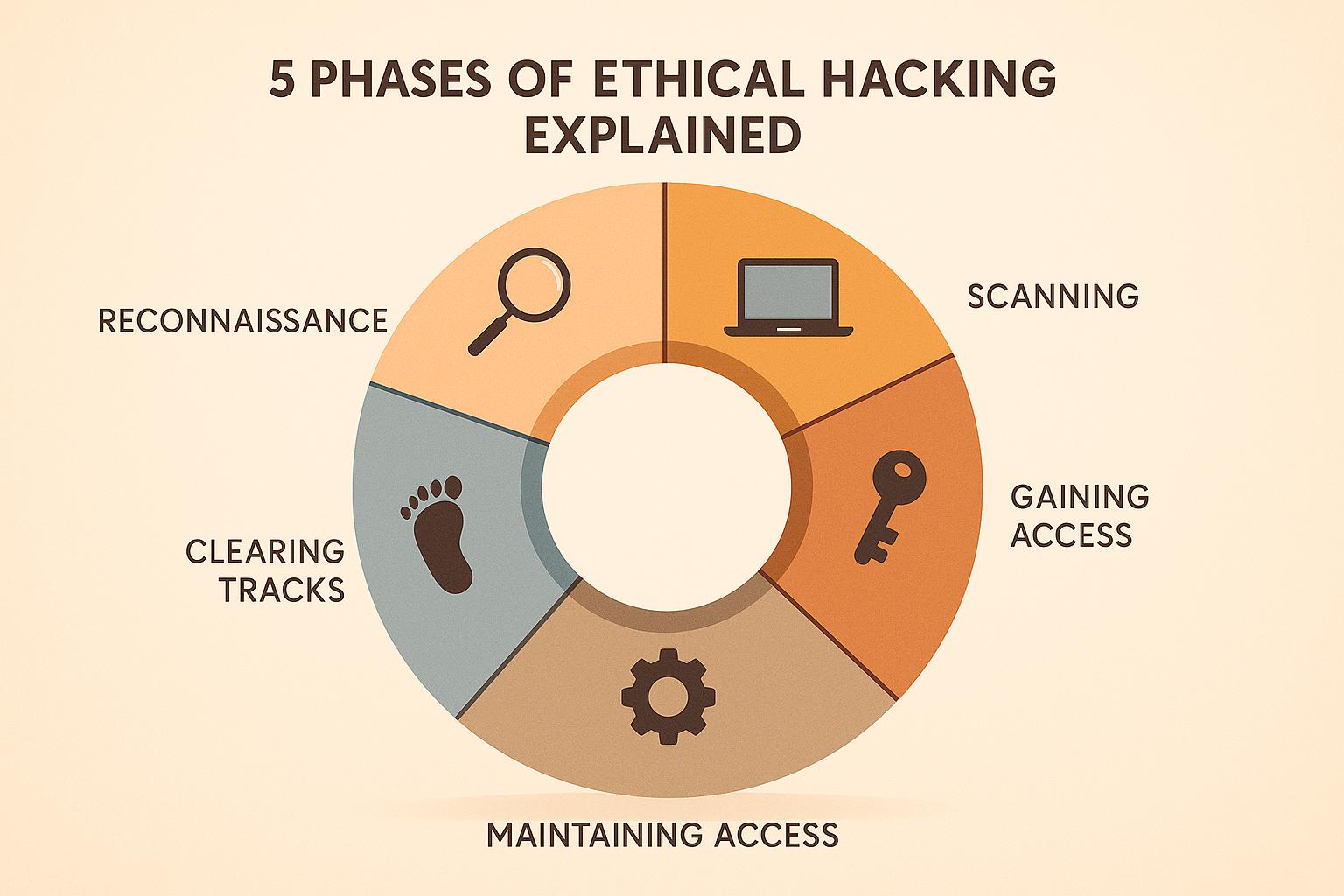
- Essential tools: Wireshark, VirusTotal, YARA, ELK Stack, and others help you gather and analyze threat data.
- Lab safety: Use network isolation, firewalls like pfSense, and follow legal guidelines when working with malware.
- Beginner projects:
- Track daily Indicators of Compromise (IOCs) from public feeds.
- Analyze phishing emails for malicious links and attachments.
- Perform static malware analysis to extract file hashes and IOCs.
- Profile threat actors like FIN7 or Lazarus Group using public reports and frameworks like MITRE ATT&CK.
These projects build practical skills for entry-level cybersecurity roles, such as SOC analyst or threat intelligence analyst. Document your work in detailed reports and create a portfolio to stand out in job applications.
Cyber Home Lab from ZERO and Catch Attackers! Free, Easy, and REAL (Microsoft Sentinel 2025)

Setting Up a Home Threat Intelligence Lab
Creating a home threat intelligence lab doesn’t require anything too extravagant - a mid-range laptop or desktop will do the trick. By using virtualization, you can run multiple operating systems as virtual machines (VMs) on a single host. This setup allows you to create isolated environments for testing, monitoring, and analysis, all while keeping your personal data and home network safe.
Hardware and Software Requirements
For smooth performance, aim for a host machine with at least 16 GB of RAM, though 32 GB is better if you plan to run several VMs and a full monitoring setup. A 500 GB solid-state drive (SSD) is ideal for storing your host operating system, VMs, and logs. It also ensures quick boot times and faster snapshot management. If you need to upgrade, adding an extra 16 GB of RAM will cost around $60 to $100.
When it comes to virtualization software, Oracle VirtualBox is a beginner-friendly option that’s free, open-source, and compatible with Windows, macOS, and Linux. It supports features like snapshots (to revert a VM to a clean state), cloning, and flexible network setups. For your lab, set up three VMs:
- A Linux workstation (Ubuntu or Kali Linux) for analysis tasks.
- A Windows VM for malware analysis (you can use a 90-day evaluation license).
- Optionally, a pfSense firewall VM for added network control.
For network stability, connect your host machine via wired Ethernet instead of Wi-Fi. A wired connection minimizes interference, making it more reliable for tasks like packet capture or intrusion detection.
Key Tools for Threat Intelligence
Once your VMs are up and running, equip them with essential tools used by professional threat analysts. These tools will help you gather, analyze, and organize data effectively:
- Wireshark: A popular tool for capturing and analyzing network traffic. It allows you to inspect HTTP requests, DNS queries, and other connections to identify potential indicators of compromise (IOCs).
- VirusTotal: This platform enables you to submit file hashes, URLs, and domains for analysis against multiple antivirus engines and sandbox environments. It’s an essential resource for enriching IOC data.
- YARA: A pattern-matching tool that helps you create custom rules to classify files based on specific strings, byte sequences, or file headers. It’s a powerful way to develop detection signatures.
- ELK Stack (Elasticsearch, Logstash, and Kibana): A centralized platform for aggregating and visualizing logs from your lab. Alternatively, consider lightweight options like Wazuh, which combines log collection with endpoint monitoring.
- Snort or Suricata: These intrusion detection systems (IDS) monitor network traffic and generate alerts when they detect known attack patterns, such as malware callbacks or exploit attempts.
- MISP or OpenCTI: Platforms for managing and sharing IOCs, offering hands-on experience with workflows used in professional threat intelligence operations.
Additionally, install Python on your analyst VM, along with a text editor like VS Code or Notepad++. These tools will help you automate tasks such as querying APIs, parsing threat feeds, and enriching IOCs.
Lab Safety and Network Isolation
Safety and network isolation are critical when working with malware samples, analyzing suspicious domains, or simulating attacks. To ensure your experiments stay contained, structure your lab with three network zones:
- WAN: The host’s internet connection.
- DMZ/Analysis: An internal or host-only network for testing.
- Management Network (optional): For administrative tasks.
Setting up a pfSense firewall VM between the WAN and DMZ can help enforce strict rules, such as allowing only necessary outbound traffic (e.g., HTTP/HTTPS lookups) while blocking inbound connections. Avoid using bridged mode for analysis VMs, as this could expose them to your home network. Instead, stick to NAT or Host-Only configurations, and disable shared folders or clipboard integrations between host and guest systems.
When storing malware samples, use password-protected ZIP or 7z archives with the password "infected." Label each archive with the malware family and date to keep your experiments organized and repeatable.
Keep legal constraints in mind. Under laws like the U.S. Computer Fraud and Abuse Act (CFAA), limit your testing to systems you own or have explicit permission to use.
Lastly, maintain good lab hygiene. Regularly patch your host and VMs, document configurations and observations in a lab notebook, and take versioned snapshots before making significant changes. Always revert your analysis VM to a clean snapshot after each session to avoid leftover artifacts that could interfere with future experiments.
Beginner Threat Intelligence Projects
With your lab set up and tools ready to go, these projects are a great way to sharpen your threat intelligence skills. Each one is designed to target specific abilities you'll use in real-world scenarios. Start with one project at a time, keep detailed documentation of your work, and build from there. These tasks are structured to complement your lab setup and help you prepare for professional roles.
Daily IOC Collection and Tracking is all about building a routine. Every day, check two or three open-source feeds like AlienVault OTX or Abuse.ch. Log the indicators of compromise (IOCs) you find in a spreadsheet or database, including the date (in MM/DD/YYYY format), source, and threat type (e.g., phishing, botnet, ransomware). Over time, you'll start spotting patterns - like recurring IP ranges, domains registered on the same day, or file hashes tied to similar malware families. This project helps you develop a habit of monitoring threat feeds and identifying recurring indicators. Once you're comfortable, move on to analyzing phishing emails.
Phishing Email Analysis helps you practice investigation techniques. Use platforms like PhishTank or GitHub to find phishing email samples and analyze them in an isolated virtual machine (VM). Extract details like sender information, URLs, and attachments. Then, verify these elements using tools like VirusTotal, URLScan.io, and AbuseIPDB. For example, you might come across a fake Microsoft login page hosted on a flagged domain, with the hosting IP linked to multiple phishing reports. Summarize your findings in a report that includes details like the sender, the lure (e.g., "urgent password reset"), malicious URLs, and hosting infrastructure. This project will teach you how to analyze email headers, investigate URLs, and perform basic malware triage. The next step? Static malware analysis.
Static Malware Analysis is all about handling malware samples safely. Download samples from sources like MalwareBazaar or VirusTotal's public repository and focus on extracting the SHA256 hash of each file - without executing them. Use tools like VirusTotal, Hybrid-Analysis, or ANY.RUN to analyze the hash. Look for detection rates (e.g., 45 out of 68 engines), command-and-control IP addresses, registry changes, and network activity. Combine your findings into a report that summarizes the malware family, its behavior, and related IOCs. This project enhances your skills in malware triage, IOC enrichment, and structured reporting. Once you've got a handle on this, broaden your perspective with threat actor profiling.
Threat Actor Profiling dives into understanding adversary behavior. Pick a known threat group like FIN7, Lazarus Group, or LockBit, and use public reports from sources like Mandiant, CrowdStrike, or CISA to create a detailed profile. Include their tactics, techniques, and procedures (TTPs), known IOCs, and targeted industries. For instance, FIN7 often targets the retail and hospitality sectors with spear-phishing emails containing malicious Word documents. Their methods include credential harvesting, lateral movement via PowerShell, and data exfiltration. Document key IOCs - such as domains, IP addresses, and file hashes - and look for patterns in their infrastructure.
These projects require only your home lab, free tools, and a few hours a week. The key is consistency. Save your reports, screenshots, and notes as you go - they'll become the foundation of your professional portfolio. These exercises align closely with the skills employers look for in entry-level SOC analyst and threat intelligence analyst roles. In the U.S., hiring managers often seek candidates who can handle IOCs, perform malware triage, analyze logs, and understand frameworks like MITRE ATT&CK. By completing these projects, you're building the hands-on experience needed to stand out. At Root School, we encourage aspiring cybersecurity professionals to use these practical exercises as a stepping stone toward landing their first job.
Daily IOC Collection and Tracking
Building a habit of collecting Indicators of Compromise (IOCs) is one of the best ways to sharpen your threat intelligence skills from home. IOCs are forensic clues that point to malicious or suspicious activity - think IP addresses, domains, URLs, file hashes, and more. Instead of trying to gather every possible IOC, focus on a few trusted public sources. Over time, you'll start recognizing patterns, understanding how attackers reuse their infrastructure, and practicing good data hygiene - key skills for any professional analyst.
Start small. Pick two or three reliable sources and make it a daily habit to check them. For example, CISA's Cybersecurity Advisories (CSAs) are a goldmine of vetted IOCs tied to major cyber campaigns, ransomware cases, and state-sponsored attacks. These advisories often include IP addresses, domains, file hashes, and detection rules (like Snort, Suricata, YARA, and Sigma). You can download IOC lists directly from CISA's website in formats like CSV or JSON or copy them from the advisory text. Be sure to tag each set with the advisory ID (e.g., "CISA AA23-XXXA") and note any referenced MITRE ATT&CK techniques.
Another excellent source is AlienVault OTX, a community-driven platform where you can subscribe to "pulses" that group IOCs with helpful metadata. These pulses provide context on malware families, threat actors, or campaigns (e.g., Emotet, Qakbot, or phishing kits). Create an OTX account, subscribe to relevant pulses, and include this step in your daily routine to stay updated on new entries.
Once you've gathered IOCs, organizing them is critical. Use tools like a spreadsheet, SQLite database, or a CSV file (e.g., "12-08-2025_otx_iocs.csv") to track your findings. At a minimum, your system should record the following:
- Indicator value (e.g., IP, domain, URL, or hash)
- Type (IP, domain, URL, hash, email, or filename)
- First seen date (MM/DD/YYYY format)
- Source (e.g., "CISA AA23-XXXA" or an "OTX pulse ID")
- Confidence level (Low, Medium, High)
- Context (e.g., malware family, threat actor, or ATT&CK technique)
- Status (Active, Expired, or False Positive)
This organized log becomes the foundation for deeper analysis in your lab.
Next, refine your data. Normalization and de-duplication are key steps that many beginners overlook. Raw IOC feeds often include duplicates, inconsistent formats, or outdated entries. Use Python libraries like pandas or csv to clean your data. If you're ready to level up, consider setting up open-source platforms like MISP or OpenCTI. MISP helps with collecting, correlating, and sharing IOCs (supporting formats like STIX), while OpenCTI focuses on mapping relationships between IOCs, malware, threat actors, and campaigns.
Adding context through enrichment transforms raw IOCs into actionable intelligence. For IPs and domains, gather geolocation data, Autonomous System Numbers (ASNs), and hosting provider details using tools like MaxMind's GeoLite database. Pair this with WHOIS and passive DNS lookups. For file hashes, public malware repositories or sandbox services can provide detection labels, behavioral summaries, and links to associated campaigns. Keep these enriched details in your tracking system to analyze trends more effectively.
To take things further, integrate your IOC database with your lab's detection systems. Export IP and domain lists as text files and load them into your lab firewall (e.g., pfSense) as alias lists or blocklists. Configure rules to block traffic tied to these indicators. For IDS systems like Suricata or Snort, convert URLs and domains into detection rules and monitor alerts. If you're using a SIEM like Wazuh or the ELK stack, build dashboards to track "Events matching known IOCs", replicating the workflow of a Security Operations Center (SOC) analyst.
Regular maintenance is essential. IOCs, especially IPs and domains, often have short lifespans. Update your tracking system regularly by marking indicators as Expired if they haven’t been observed in 30 to 90 days. Document false positives (e.g., a legitimate cloud service IP flagged due to shared infrastructure) and adjust confidence ratings accordingly. This ongoing lifecycle management mirrors the practices of professional analysts.
Finally, treat your IOC tracking log as more than just a technical exercise - it’s a portfolio piece. Stick to a consistent format and write short weekly summaries highlighting your findings, the threats tied to your IOCs, and the detection measures you’ve implemented. For U.S. job applications, showcasing your experience with CISA advisories, AlienVault OTX, and platforms like MISP or OpenCTI can demonstrate hands-on experience with real-world threat data. At Root School, we encourage students to turn these daily exercises into resume bullet points and interview stories, showing employers that they’ve worked with the same tools and workflows used in professional SOC and threat intelligence roles. Keep your log updated to support ongoing analysis and detection efforts in your lab.
Static Malware Analysis
Static malware analysis involves examining suspicious files without actually running them. Unlike dynamic analysis, where malware is executed in a controlled environment to observe its behavior, static analysis keeps the malware inactive. This approach is safer and quicker, requiring minimal infrastructure, making it ideal for beginners and those working in smaller setups.
Static analysis allows you to extract critical Indicators of Compromise (IOCs) - such as file hashes, embedded domains, IP addresses, and suspicious strings - without the risk of accidental infection or network compromise. These IOCs become essential components of your threat intelligence work, seamlessly integrating into your tracking systems.
Setting Up Your Static Analysis Environment
To get started, you'll need an isolated environment. Use a dedicated virtual machine (VM) for analysis tasks, created with a hypervisor like VirtualBox. Ensure the VM is air-gapped by disabling the network adapter or setting it to "Host-only" mode. This setup prevents any accidental communication with external servers or your personal devices.
Your VM can run a standard operating system like Windows 10 or Ubuntu Linux. Windows is often preferred since most malware targets this platform, but Linux offers powerful command-line tools. After setting up the VM, take a clean snapshot so you can easily revert to a pristine state after each session, ensuring no leftover malware affects future work.
Safely Obtaining Malware Samples
When acquiring malware samples, stick to controlled and reputable sources. Some reliable options include:
- VirusShare: Offers hash-based access to malware samples after registration.
- Malware Traffic Analysis: Provides pcap files and malware samples with contextual information.
- SANS Internet Storm Center: Supplies curated samples for educational purposes.
These repositories often distribute samples in password-protected archives, typically using "infected" as the password. This precaution minimizes the risk of accidental execution. Always download and handle these files within your isolated VM, and maintain a detailed record of each sample’s source, hash, and analysis date.
Extracting File Hashes
File hashes are unique cryptographic fingerprints that help identify files. Even a minor change to a file alters its hash completely. Use tools like PowerShell's Get-FileHash on Windows or commands like md5sum, sha1sum, and sha256sum on Linux to generate MD5, SHA-1, and SHA-256 hashes. If you prefer graphical tools, HashTab or HashMyFiles are good options.
Document details such as the filename, file size, source, and analysis date in a standardized report. Hashes allow you to track whether a sample has been analyzed before and cross-reference it with other analyses.
Cross-check your extracted hashes using VirusTotal, a free platform that aggregates results from multiple antivirus engines. Paste the hash into VirusTotal to see if the sample is known, how many engines flag it as malicious, and what names vendors assign to it. This step not only confirms the sample's malicious nature but also provides initial insights into its classification.
String Extraction for Deeper Insights
String extraction uncovers human-readable text within binary files, such as URLs, IP addresses, file paths, registry keys, and error messages. These strings often reveal valuable IOCs, such as command-and-control servers, hardcoded credentials, or debugging information, without requiring execution.
- On Windows, use Sysinternals Strings to extract strings from executables (
strings.exe sample.exe > output.txt). - On Linux, use the
stringscommand (strings sample.bin > output.txt). - For obfuscated or encoded strings, FLOSS (FireEye Labs Obfuscated String Solver) is a powerful tool.
Look for patterns that indicate malicious intent. For example, domain names and IP addresses may point to communication endpoints, while file paths like C:\Windows\Temp\ or %APPDATA%\ suggest installation locations. Registry keys often reveal persistence mechanisms, and user-agent strings can indicate how malware disguises its traffic. Focus on strings that stand out - unusual domains, encoded data, or references to security software.
Validating and Organizing Findings
Validation is key to ensuring the accuracy of your findings. Use tools like WHOIS, AlienVault OTX, or Shodan to verify extracted domains and IPs. Check for matches with known malware signatures using YARA rules or MISP databases. Compare your results with public analysis reports from sources like Malwarebytes Labs or Cisco Talos. Assign confidence levels to each IOC based on validation:
- High confidence: Corroborated by multiple sources.
- Medium confidence: Supported by reliable sources.
- Low confidence: Isolated observations.
Organize your findings in a structured format, including details like sample hashes, file size, source, analysis date, and key IOCs. If applicable, map findings to MITRE ATT&CK techniques to provide additional context. For instance, registry keys might align with T1547 (Boot or Logon Autostart Execution).
Store your reports in a searchable format. Begin with a simple folder structure (e.g., "12-08-2025_ransomware_sample") and include the sample hash, analysis report, and extracted artifacts. As your collection grows, consider using tools like MISP or a master spreadsheet for better indexing.
Avoiding Common Mistakes
Static analysis requires careful attention to detail. Avoid the following pitfalls:
- Accidental execution: Never open malware files directly or in the wrong application.
- Compromised isolation: Always verify your VM’s network isolation before analysis.
- Lack of context: Understand the source and purpose of each sample to avoid incomplete analysis.
- Poor documentation: Record every step to ensure your work is reproducible and referenceable.
Keep your tools and VM updated to protect against vulnerabilities. Importantly, only analyze samples you have explicit permission to work with, and adhere to laws like the Computer Fraud and Abuse Act (CFAA). Using legitimate repositories like VirusShare or SANS ensures you stay on the right side of the law.
For building a portfolio, select three to five of your most thorough analyses. Include screenshots of processes like hash extraction, string analysis, and VirusTotal results. Clearly explain your conclusions and validation steps. These polished reports showcase your methodical approach and ability to extract and validate IOCs effectively.
sbb-itb-8a31326
Threat Actor Profiling
Threat actor profiling involves gathering, organizing, and documenting detailed information about adversary groups, including their tactics, tools, infrastructure, and typical targets. This process helps you think like a professional analyst by using open-source intelligence (OSINT), mapping behaviors to frameworks like MITRE ATT&CK, and identifying indicators of compromise (IOCs) you can test in a controlled environment. For those running a home threat intelligence lab, profiling mirrors the work done in entry-level threat intelligence or Security Operations Center (SOC) roles, while also providing valuable examples for a portfolio.
Choosing Your First Threat Actor
Start by focusing on well-documented public threat groups. The MITRE ATT&CK framework maintains detailed profiles for over 100 named groups, such as APT28, APT29, FIN7, and Lazarus Group. Each profile includes techniques, tools, and targeted industries, making them a great starting point.
Select a group based on reliable open reporting from sources like Mandiant, CISA, or Microsoft. Look for groups whose techniques - like phishing, PowerShell usage, or credential dumping - can be safely simulated in a home lab without violating any laws. Choose groups relevant to industries you're interested in, such as finance, healthcare, or small businesses. Begin with a prominent Advanced Persistent Threat (APT) or financially motivated group, and later explore regional or niche actors to broaden your understanding.
Building a Research Workflow
Profiling a threat actor requires a structured approach. Here’s a practical workflow:
- Identify the group: Use the MITRE ATT&CK "Groups" page to find aliases, descriptions, and targeted sectors.
- Extract techniques: List the group’s known ATT&CK techniques and sub-techniques, such as T1566.001 (Spearphishing Attachment) or T1059 (Command and Scripting Interpreter).
- Collect public reports: Search for vendor and government reports using terms like "APT28 report pdf." Record key details like intrusion sets, campaigns, malware families, and infrastructure patterns.
- Pull IOCs: Gather domains, IPs, hashes, file names, and artifacts for lab use. Use these only for detection and enrichment practice - never for malicious purposes.
- Cross-check sources: Validate findings using platforms like MISP or OpenCTI to identify overlaps or discrepancies in techniques and tools.
Document your findings in a structured format, including an overview, techniques, infrastructure, IOCs, and notable campaigns. This groundwork prepares you for aligning behaviors with standardized frameworks.
Mapping Behavior to MITRE ATT&CK
To map a threat actor’s behavior, analyze incident reports for key actions like "used malicious Excel attachments", "dumped LSASS memory", or "used C2 over HTTPS." Match these behaviors to ATT&CK tactics (e.g., Initial Access, Execution, Persistence) and their corresponding technique IDs. Create a table or diagram that outlines the connections:
- Tactic → Technique ID → Description → Evidence/Source
Tools like MITRE ATT&CK Navigator can help you visualize the actor’s behavior. Save these visualizations as layers to include in your portfolio, showcasing your ability to apply industry-standard frameworks.
Structuring Your Threat Actor Profile
A professional threat actor profile typically includes:
- Actor Overview: Names, aliases, suspected origin, motivations (e.g., espionage, financial gain, hacktivism), and target industries.
- TTPs: Mapped tactics, techniques, and procedures (TTPs) with real-world examples from reports.
- Malware and Tools: Details on custom malware families, open-source tools, and frameworks like Cobalt Strike or Metasploit.
- Infrastructure: Common domain patterns, hosting providers, command-and-control (C2) methods, and phishing infrastructure.
- Indicators of Compromise: IPs, domains, hashes, file paths, and registry keys for detection practice.
- Notable Campaigns: Summaries of key operations, timelines, and impacts.
- Detection and Mitigation Ideas: Log sources, Sigma-like rules, and YARA rules for malware families.
A 2023 SANS Institute survey revealed that 78% of security teams use MITRE ATT&CK for threat modeling and adversary emulation, underscoring its importance for home lab projects.
Working Safely with Real-World IOCs
When handling real-world IOCs, prioritize safety. Treat IOCs as data only, storing and analyzing them in your lab SIEM or threat intelligence platform without connecting to live malicious infrastructure. For detection logic, use test or sinkholed infrastructure - such as local DNS entries resolving malicious domains to non-routable IPs.
Keep your lab isolated from your home network by using hypervisors or virtual switches. Adding a virtual firewall like pfSense can further protect your setup, ensuring accidental communication with external servers or personal devices is avoided. This setup allows you to safely practice realistic detection and analysis workflows.
Organizing and Enriching Your Research
To deepen your analysis, leverage enrichment tools and platforms. Open-source tools like MISP or OpenCTI help store, tag, and correlate IOCs and events, making them ideal for organizing threat actor profiles. Use APIs like VirusTotal, AbuseIPDB, and URL scan services to look up hashes, IPs, and domains found in reports. Implement detection rules with YARA for malware families or Sigma-style rules for log-based detections.
These tools can run on basic hardware with virtualization, making them accessible for home labs while aligning with practices used in enterprise environments.
Creating Portfolio-Ready Case Studies
Each threat actor profile can serve as a case study that mirrors real-world analyst work. Write a clear, concise report with an executive summary, actor overview, ATT&CK mapping, key IOCs, and detection recommendations. Share sanitized versions of these reports in a portfolio or Git repository, ensuring no live malicious links are included.
In interviews, explain your process - from source selection and ATT&CK mapping to tool usage (e.g., MISP, ELK, Suricata) - and highlight what you learned about the actor’s methods. This demonstrates your ability to follow analytical workflows similar to those in real-world cybersecurity roles.
Following an Incremental Learning Path
Breaking the process into manageable steps makes it easier to build your skills over time:
- Week 1: Choose an actor, read two or three public reports, and create a one-page summary of their motivations, targets, and tools.
- Week 2: Map the actor’s techniques to MITRE ATT&CK and document them in a table.
- Week 3: Supplement your research with vendor reports from sources like Mandiant or CrowdStrike, and enrich the profile with OSINT.
- Week 4: Set up a threat intel platform like MISP or use a spreadsheet to organize IOCs. Write a detection rule or YARA signature based on the actor’s known tools.
This step-by-step approach builds confidence and provides tangible outputs for your portfolio.
Maintaining Current Profiles
Threat actor profiles require regular updates as new campaigns and techniques emerge. Many groups reuse infrastructure, tools, and TTPs, allowing analysts to build consistent profiles over time. Schedule quarterly reviews to check for updated reports, ATT&CK mappings, or new campaigns.
Document changes, such as new techniques or shifts in targeting, to practice continuous analysis. Keeping profiles current shows your commitment to staying informed about evolving threats, a vital skill for threat intelligence professionals.
Using Professional Frameworks in Home Projects
To showcase your readiness for the industry, leverage established frameworks like MITRE ATT&CK, STIX/TAXII, and professional reporting methods. These tools help elevate your home lab projects, turning raw data into structured, actionable insights. By presenting your findings in a way that mirrors real-world security workflows, you demonstrate your understanding of professional standards and practices.
Mapping Findings to MITRE ATT&CK
MITRE ATT&CK is the go-to framework for describing adversary behavior. Whether you're analyzing a phishing email, testing malware, or simulating an attack in your lab, start by identifying observable actions and mapping them to relevant ATT&CK tactics and techniques.
For instance, if you're examining a phishing email, break down its key actions - delivery, execution, persistence, and credential theft. Then, align each action with its corresponding ATT&CK technique. For example:
- T1566 Phishing: Initial access
- T1204 User Execution: Opening the malicious attachment
- T1053 Scheduled Task/Job: Persistence
- T1056 Input Capture: Credential theft via a fake login page
Use tools like Wireshark and Sysmon to gather evidence for each mapped technique. To keep things organized, create a spreadsheet or markdown file with columns for project name, observed behavior, ATT&CK tactic, technique ID, and evidence (e.g., log snippets or screenshots). This "ATT&CK mapping sheet" mirrors professional documentation and can become a valuable part of your portfolio.
For more complex scenarios, document an entire attack chain - from initial access to data exfiltration. For example, you could simulate a phishing attack that leads to a credential harvester on an isolated virtual machine, followed by a harmless script mimicking data exfiltration. Record each phase, noting how access was gained, code executed, persistence established, and data exfiltrated. Map each phase to relevant ATT&CK techniques to create a detailed timeline of events.
To visualize your findings, use the ATT&CK Navigator - a free web tool. Create a layer file, color-code observed techniques (e.g., green for detected, yellow for partial visibility, and red for gaps), and export the results as a JSON file or screenshot for your portfolio.
With an extensive matrix covering tactics, techniques, and threat groups, MITRE ATT&CK provides endless material for home projects. Each technique page includes detection tips, relevant data sources (e.g., PowerShell logs), and examples of real-world threat actors, which you can use to write realistic threat profiles connecting your lab work to documented campaigns.
Organizing IOCs Using STIX/TAXII
STIX 2.x and TAXII 2.x are standards for representing and sharing cyber threat intelligence. Even if you don’t have a full STIX/TAXII server at home, you can still demonstrate your knowledge by creating a simplified version.
Start by building a STIX-like template to catalog your Indicators of Compromise (IOCs). Include fields like:
- Indicator type (IP, domain, hash, YARA rule)
- Value
- First seen date (MM/DD/YYYY)
- Last seen date
- Confidence level (low, medium, high)
- Related ATT&CK techniques
- Source (e.g., your lab project or a vendor report)
Group related indicators into logical sets that reflect campaigns or intrusion patterns. For instance, if you're profiling a specific threat actor, include their typical infrastructure, malware families, and targeting methods. Use Git on platforms like GitHub to version your IOC collections, treating updates as new STIX "bundles" to mimic professional workflows.
To simulate TAXII's publish-subscribe model, use a GitHub repository or shared folder as your "feed." Define a simple JSON or CSV format with fields like indicator type, value, and related techniques. You can even write a Python script to filter data by type or date and generate lists of indicators for defensive tools like pfSense or Suricata.
If your hardware allows, experiment with tools like MISP or OpenCTI on a Linux VM. These platforms let you store IOCs, tag them with ATT&CK techniques, and import/export feeds. Skills gained here directly translate to enterprise platforms like Splunk ES or Microsoft Sentinel, which often include native ATT&CK and STIX/TAXII integrations.
Writing Professional Reports
The final step in any home project is documenting your findings in a professional report. This is a critical skill for roles like threat intelligence analysts and incident responders. Your report should follow a structured format similar to those used in the industry:
- Executive Summary: A concise overview of what you did, what you discovered, and its potential impact. Use plain language and frame the risks in terms of business consequences, like account compromise or financial loss.
- Scope and Methodology: Describe your lab setup, including the tools (e.g., Wireshark, Sysmon, Suricata, YARA), operating systems, and any limitations or assumptions.
- Technical Analysis: Provide a detailed breakdown of your observations. Include screenshots, log excerpts, network diagrams, and command outputs to support your findings. Map each action to relevant ATT&CK techniques.
- MITRE ATT&CK Mapping: Summarize your ATT&CK mappings, showing how each observed behavior aligns with specific tactics and techniques.
- IOCs and Artifacts: List the indicators you discovered, along with their context and relevance.
- Impact and Risk: Explain the potential consequences of the threat in a real-world setting.
- Recommendations: Offer actionable steps for mitigating similar threats.
For additional resources on writing professional reports and aligning your work with industry standards, check out Root School. This practice not only sharpens your skills but also builds a portfolio that showcases your ability to think and communicate like a professional.
Building a Portfolio from Home Projects
Using your hands-on lab experiences, you can create a portfolio that showcases your readiness for threat intelligence roles. A well-documented portfolio goes beyond listing tools - it demonstrates your analytical skills, technical expertise, and ability to communicate findings clearly. Hiring managers want evidence of your abilities, not just a rundown of software you've used. By documenting your projects effectively, you can turn your practice sessions into proof that you’re prepared to handle the demands of a threat intelligence analyst.
Once your lab setup is in place and your projects are underway, the next step is to document your work in a way that transforms it into a professional portfolio.
Maintaining a Lab Journal
A lab journal is where you record your daily activities, objectives, and lessons learned. Think of it as your personal logbook, capturing your steps and insights in real-time. This practice not only mirrors how professional analysts document investigations but also makes it easier to transform raw notes into polished portfolio pieces later.
Start each journal entry with a clear header that includes essential metadata: the date (MM/DD/YYYY), project name, your role (e.g., analyst, incident responder, CTI researcher), and details about your lab environment (such as the VMs, operating systems, or network setup you used). This context is invaluable for both you and anyone reviewing your work - especially when preparing for interviews.
Follow the header with a brief objective or hypothesis. For example: “Identify command-and-control patterns in remote access trojan samples from public malware repositories” or “Track phishing infrastructure in a simulated credential harvesting campaign over 14 days.” This frames your work with a clear purpose, showing that your efforts are intentional and goal-oriented.
Document your data sources and collection methods, specifying where your information came from, such as OSINT feeds, public sandboxes, or honeypots. If you’re using tools like VirusTotal, MalwareBazaar, or personal spam traps, mention them explicitly. This not only demonstrates transparency but also highlights your ability to work with real-world intelligence sources.
Next, record your methods and tools in detail. List the commands you ran, configurations you adjusted, and queries you executed. For example, if you used Wireshark to analyze PCAP files, note the display filters applied. If you correlated IOCs in MISP, explain how you tagged and organized them. Screenshots of key moments - like detection alerts or ATT&CK mappings - are also valuable additions, as they provide visual evidence of your work. This level of documentation shows your ability to follow and create repeatable procedures, a critical skill in threat intelligence roles.
In the findings section, summarize the key IOCs, TTPs, and ATT&CK technique IDs you uncovered. Include simple metrics like the number of unique IPs or domains tracked or the frequency of specific techniques. For instance: “Tracked 220 unique IPs and 45 domains over 14 days, clustering them into three campaigns using WHOIS patterns and timing analysis. Mapped activity to MITRE ATT&CK T1566 (Phishing) and T1204 (User Execution).”
Finally, add interpretation and reflection. Discuss what your findings suggest - whether the activity indicates commodity malware or something more targeted - and outline possible next steps for further investigation. Wrap up with a few bullet points summarizing lessons learned, mistakes made, and ideas for improvement. This reflective process not only deepens your understanding but also provides excellent material for interviews, showcasing your attention to detail and growth mindset.
Store your journal digitally using tools like Markdown files, OneNote, Notion, or Obsidian. Use tags to organize entries by topics such as malware analysis, phishing, or ATT&CK techniques. This makes it easier to compile related notes into comprehensive case studies or reports for your portfolio.
Saving and Showcasing Project Outputs
Every project you complete should generate artifacts that highlight your skills in threat intelligence. These outputs form the backbone of your portfolio, showing not just what you know but what you can produce.
Start with a final report. Save it in PDF or Markdown format, and structure it like a professional incident or intelligence report. Include an executive summary, scope and methodology, technical analysis with screenshots, ATT&CK mappings, IOC lists, impact assessments, and recommendations. This demonstrates your ability to organize complex information and communicate it effectively to both technical and non-technical audiences.
Create IOC tables to document domains, IP addresses, file hashes, and registry keys, along with relevant context. Include fields like indicator type, value, first seen date (MM/DD/YYYY), last seen date, confidence level, related ATT&CK techniques, and source. You can export these from tools like MISP or OpenCTI, or build them manually in CSV or JSON format. Well-structured IOC tables highlight your ability to normalize and share threat data.
Save visual artifacts that illustrate your analysis. For example, export ATT&CK heatmaps to show observed techniques and gaps, create timelines of campaigns, or draw network diagrams of your lab setup. Screenshots of SIEM dashboards, detection alerts, and correlation searches are also valuable - just ensure you redact sensitive details like real IPs or hostnames.
If you create scripts or automation, such as Python scripts for enriching IOCs or PowerShell scripts for parsing logs, host them on a public GitHub repository. Include clear README documentation that explains what each script does, how to run it, and any dependencies. This demonstrates your coding skills and your ability to streamline processes.
Organize all your materials in a clear folder structure, such as:
/Portfolio/01-IOC-Tracking→ Subfolders forReport,Data,Screenshots, andCode/Portfolio/02-Malware-Analysis→ Subfolders forReport,Data,Screenshots, andCode/Portfolio/03-Threat-Actor-Profiles→ Subfolders forReport,Data,Screenshots, andCode
This structure makes it easy to share specific projects with employers or link them on your resume or LinkedIn profile. You can also host detailed write-ups and PDF case studies on a personal website or blog to establish a professional online presence.
When publishing your work, prioritize safety and legality. Use only public malware samples from sources like MalwareBazaar or ANY.RUN, or synthetic data generated in your isolated lab. Never expose real client data, employer logs, or information covered by NDAs. Redact aggressively, and include a disclaimer stating that all work was conducted in an isolated lab with explicit permission, following legal and ethical guidelines.
Highlighting Skills for Job Applications
Once your projects are documented and organized, the final step is to translate them into resume-friendly language that appeals to hiring managers and applicant tracking systems (ATS). Your portfolio is most effective when it clearly aligns with the skills employers are looking for.
On your resume, include a section titled "Cybersecurity Projects" or "Threat Intelligence Projects." For each project, write two to four bullet points that start with strong action verbs such as Analyzed, Developed, Implemented, or Profiled. Focus on measurable achievements like “analyzed 5 GB of data,” “curated over 120 IOCs,” or “profiled a threat actor across four public campaigns spanning 2022–2024.” This approach ensures your home lab experience resonates with potential employers.
Conclusion
Home threat intelligence projects offer an excellent way to build practical cybersecurity skills without breaking the bank. By blending hands-on lab work, established professional frameworks, and detailed documentation, these projects transform casual learning into tangible experience that U.S. employers actively seek in entry-level roles like SOC analyst, threat intelligence analyst, and incident responder.
Activities such as daily tracking of indicators of compromise (IOCs), static malware analysis, and profiling threat actors are more than just exercises - they’re opportunities to develop and refine the core skills these roles demand. These projects directly tie into the earlier discussions on setting up labs and executing meaningful tasks. Each activity, whether it’s tracking IOCs or creating detailed threat profiles, reinforces the skills this guide has highlighted.
Using structured frameworks like MITRE ATT&CK allows you to turn your lab findings into actionable intelligence that mirrors enterprise standards. Writing up each project in a professional format - with an executive summary, methodology, findings, ATT&CK mappings, and recommendations - prepares you for real-world communication. This habit of treating every exercise as if it’s for a manager or client not only sharpens professionalism but also creates work products that hiring managers immediately recognize as valuable.
Getting started doesn’t require a huge investment. Tools like VirtualBox, open-source Linux distributions, and free platforms like MISP, OpenCTI, Suricata, and Snort let you dive in with minimal costs. You can scale up gradually - adding more RAM or an external SSD as your projects grow in complexity. Even single-VM tasks, like log analysis, creating YARA rules, or tracking phishing domains, can become standout portfolio pieces when paired with proper documentation.
Your documented work becomes the foundation of a strong portfolio. Keeping a concise lab journal and saving key artifacts - such as PCAP files, screenshots, and detailed reports - transforms your everyday efforts into a showcase of your skills. For entry-level SOC and CTI roles, portfolios showcasing real projects often carry more weight than certifications alone. Platforms like Root School can help you translate your lab work into polished resumes, LinkedIn profiles, and compelling interview stories tailored to the U.S. job market.
To get started immediately, set a simple goal for the next 48 hours: track 10 suspicious IPs or domains, map behaviors to three MITRE ATT&CK techniques, and document your findings in a lab journal. Create one small artifact - whether it’s a one-page report, a screenshot of your IOC tracker, or a diagram of your lab setup - that can later enhance your portfolio. This actionable checklist bridges the gap between theory and practice, helping you take the first steps toward a cybersecurity career.
FAQs
What mistakes should I avoid when building a home threat intelligence lab?
When building a home threat intelligence lab, there are a few missteps you’ll want to avoid to make the process smoother and more effective.
First, keep it simple. It’s tempting to dive in with a ton of tools and features, but starting small is the way to go. Focus on the basics and expand your setup as you gain confidence and experience. Overloading your lab with too many tools right away can make things chaotic and harder to manage.
Second, make sure your lab is completely isolated from your main network. This step is non-negotiable. Without proper isolation, you risk exposing your personal devices to potential threats during testing. A virtualized environment or a separate network dedicated to your lab is a smart way to keep everything secure.
Finally, don’t underestimate the importance of documentation. Keeping organized notes on your configurations, tools, and discoveries will save you time troubleshooting and help you track your progress. Plus, detailed records can serve as a portfolio to showcase your skills down the line.
How can I make sure my home threat intelligence projects follow legal guidelines?
To make sure your home threat intelligence projects align with legal requirements, begin by understanding the relevant local, state, and federal laws in the U.S. that govern cybersecurity and data privacy. Actions like scanning networks, gathering data, or analyzing threats should only be carried out on systems that you own or have clear permission to access.
Additionally, steer clear of accessing or storing sensitive or personal information without proper authorization. If you're unsure about what’s allowed, consult with legal experts or rely on reputable resources to get clarity. Staying informed and careful ensures you approach threat intelligence in an ethical and responsible way.
What’s the difference between static and dynamic malware analysis, and when should you use them?
Static malware analysis involves examining the malware's code without executing it. This approach provides a quick way to understand the malware's structure, functionality, and any potential indicators of compromise. It’s often the go-to first step when assessing a threat.
Dynamic malware analysis takes things a step further by running the malware in a controlled environment, such as a sandbox. This allows analysts to observe its behavior firsthand - like how it communicates over a network or attempts to evade detection mechanisms.
A good strategy is to start with static analysis for a quick overview, then move to dynamic analysis when you need a closer look at how the malware operates or tries to bypass defenses.